How do hackers utilize your data, and how can it harm you?
The cyber-attacks on
financial and services institutions have raised questions about the safety of
consumer data. According to people associated with the cyber security sector,
the comprehensive security system against cyber-attacks in Pakistan is weak.
Cyber security experts say that at the
individual level, organizations have adopted a system against cyber-attacks,
but at the national level, there is no cyber security response mechanism that
can be mobilized against such attacks.
Many Pakistani
institutions, banks, and significant corporations are also targets of
cyber-attacks, according to Pakistan's Federal Minister for Information
Technology.
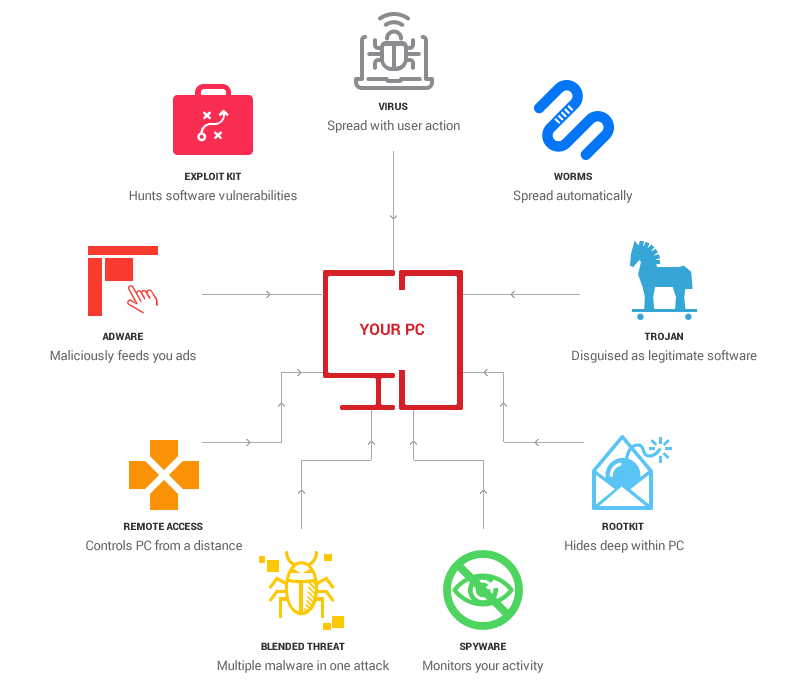
How does a cyber-attack
happen?
Regarding how cyber-attacks
are carried out on government institutions, banks and companies, cyber security
experts say that the systems operating in the institutions are connected to the
internet but these systems are very vulnerable to cyber security attacks.
Experts say that
when hackers attack an organization's system, they lock the data of those
organizations and turn it into a machine language and then no one but them can
open this data.
Experts say that
they hack into the system of organizations by turning it into ransomware and
this whole operation is used to demand ransom. Hackers demand ransom from
organizations to restore the hacked system.
According to the reports, if the system of an organization is hacked, the existing data is compromised and then a new system has to be created so that the data can be recovered. However, hackers frequently damage data, making it impossible to recover.
The Federal Minister
for IT said that with the increasing use of technology and online activities
around the world, cybercrime is also on the rise. If you look at the
international statistics, you can see the seriousness of the cyber security
situation.
Every day, millions
of cyber-attacks occur throughout the world, with ransomware accounting for
more than 550,000 of them. Last year, these cyber-attacks caused a loss of 20 billion
dollars worldwide.
According to Federal
Minister, there are hundreds of small and big cyber-attacks in Pakistan every
day which is thwarted by our experts. However, we will need to grow the number
of these specialists over time. Such assaults demonstrate how vulnerable our
institutions' and consumers' data are. If the institutions continue to ignore
the Ministry of IT's recommendations, irreversible damage might result.
Read also: PSL 7: Who will play for which team, and how can you get tickets?
How is the stolen
data used?
Experts say that the
dark web is the underworld of the internet world where this data is put in
order to be used for criminal purposes. ۔ If the data of an institution, a bank, or a
government agency, is stolen and put on the dark web, then the data of the
customers of the bank or the persons in the government agency put such persons
at great risk.
Experts say that the arrival of people's account numbers and other personal information on this dark web means that their personal security and the protection of their property are at risk. Money can also be withdrawn from their bank account and on the other hand, they can be blackmailed based on the money in their accounts. In some cases, the system is hacked and the money is withdrawn from the banks.
A few months ago, the FBR website was hacked and the most important data was compromised. In June last year, a well-known Pakistani music streaming website was cyber-attacked and hackers released data on 257,000 users on the Dark Web.
A year ago, K-Electric's system was hacked and a ransom was demanded. Similarly, the data of some banks was hacked but the bank asked the customers to change their PIN codes immediately which minimized the losses.
How are ordinary
people and consumers affected by cyber-attacks?
After the cyber-attack
on the National Bank system, the State Bank of Pakistan said in a message on
Twitter that the National Bank did not report any financial loss after the
attack.
According to the National Bank, immediately after the attack, experts worked to repair any possible damage from the attack and to restore the system.
The cyber security expert said that when data on government agencies, banks, and companies are harmed by cyber-attacks, the data on consumers and citizens are stolen and put on the dark web. If so, their personal security and the protection of their savings are compromised.
According to the experts, although in case of a cyber-attack on a bank, if money is withdrawn from the customer's account, under the SBP law in Pakistan, the bank refunds the money to the customer as there is no fault of the customer. However, he pointed out that if a bank's data is stolen and put on the Dark Web, then users who have significant amounts of money in their accounts are at greater risk and could be blackmailed accordingly. Similarly, government agencies that have citizens' data and details of their assets, if they come to the Dark Web, criminal gangs can achieve their goals by intimidating people based on it.
Read also: What is Web 3.0 | How will it replace the Internet?
Is there an
integrated security system at the national level against cyber-attacks?
Cyber security experts said that just as
Pakistan has an army at the national level to deal with an internal and
external enemy that protects the people, there is no cyber security response
mechanism at the national level along these lines. Institutions and banks
individually have mechanisms in place to protect their data against cyber-attacks,
but there is no such integrated system at the national level.
In India, there are
two national mechanisms against cyber-attacks, while in Bangladesh a system is
fully operational.
Ministry of IT is forming a 'Computer Emergency Response Team' at the national and regional levels. The team is made up of cyber security experts and will respond immediately to hacker attacks. The cyber team will also provide all possible technical support to every Pakistani public and private institution. It is important that every organization implements a cybersecurity setup in its system on a priority basis.
The Federal Minister for Information Technology went on to say that we need to build an integrated structure so that any cyber-attack on any public or private entity in Pakistan is not only halted but also responded against.
information security, computer security, it
security, cyber-attacks, threat intelligence, digital
security, national cyber security centre, cyber threat
intelligence, cyber threats, cyber-attacks today, top
cybersecurity companies, cyber security threats, cyber security
services, cyber defense, pcysys, cyber breach, cyber
security attacks, cyber security course, what is cyber security
pdf, types of cyber security, cyber security ppt, cyber security
awareness, cyber security definition, cyber security
introduction, ethical hacking, cybersecurity, cyber
security salary, cyber security news, cyber security companies, what
do hackers use your data for, what do hackers want, what do hackers
do with stolen data, what do hackers use to hack, what do hackers
look like, what do hackers use computer viruses for, what do hackers
study, hacker definition, hacker typer, hacker
halted, hacker news, hacker school, hacker rank, hacker
software, hacking tools, hacking definition, hacking
books, hacking techniques in cyber security, hacking
websites, hacking tutorials, hacking news, hacking course, cybersecurity
and infrastructure security agency










0 Comments